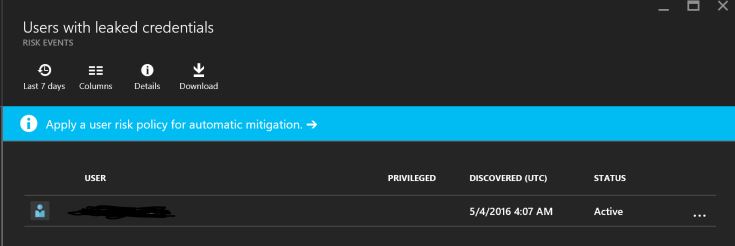
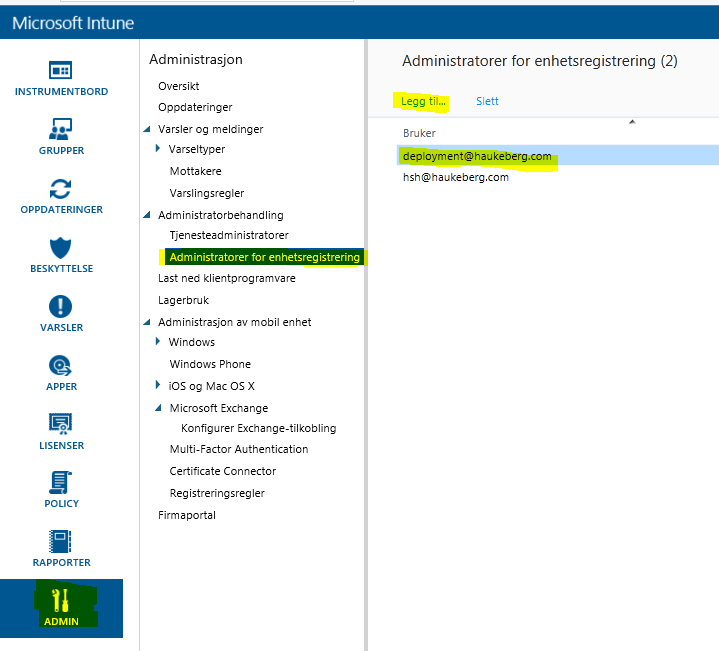
In Azure AD you have this service called Cloud App Discover. It consist of an agent you install on a local machine and a web service which polls the data and visualizes it.
Take a look at this:
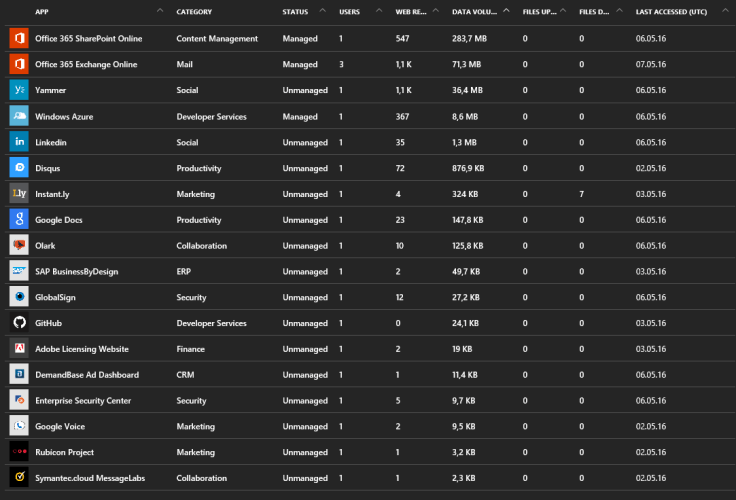
This service is a great way to discover what your employees/users/students/family really uses and how much they use it. e.g. You have bought Google apps, but your users use OneDrive or Box.
You can read more here: https://azure.microsoft.com/nb-no/documentation/articles/active-directory-cloudappdiscovery-whatis/
I did not know I even used all these services. And best of all you can manage them with Azure AD which means you can use your Office 365 credentials to logon to these services.
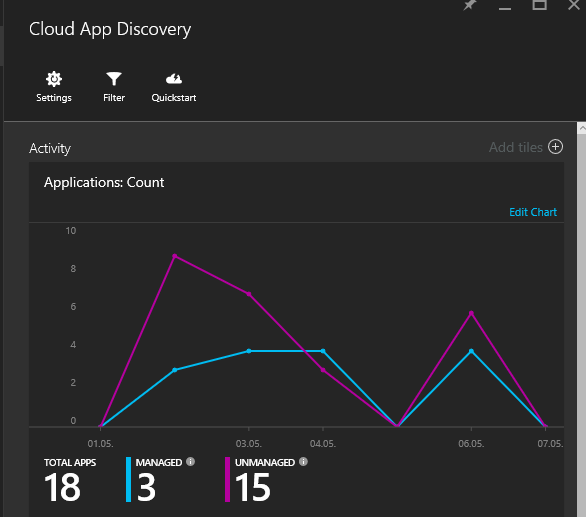
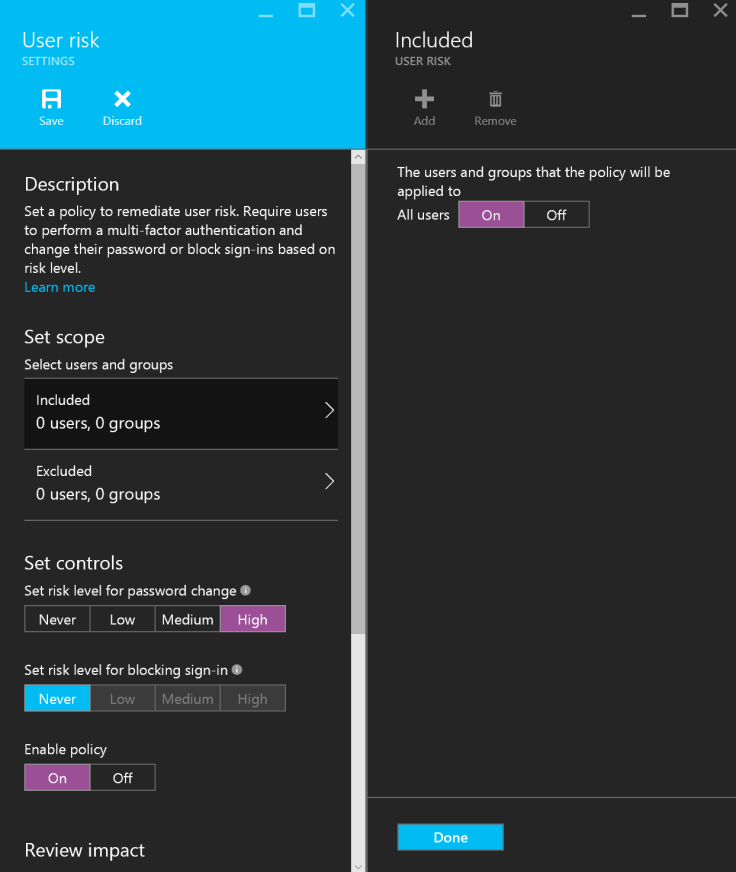
Here is how you set up cloud discovery on a local machine:



Remember that if you want to distribute this application you need to include the CERT file as well.













You must be logged in to post a comment.