Dersom du har bestilt lisenser på en volumlisensavtale med Microsoft så må lisensene ofte aktiveres inne på VLSC.
- for å logge deg på VLSC går du hit: https://www.microsoft.com/Licensing/servicecenter/default.aspx
- her må du logge deg på med din Microsoft konto. Dette har ikke noe med Office 365 eller Microsoft Intune å gjøre. Du må velge den private “live-ID’en” som du har opprettet for å logge deg på her.
- Når du har logget deg inn så kan du starte aktiveringen ved å trykke på “Aktivering av elektronisk tjeneste”
- Dersom du ikke finner lisensene er dette oftest fordi du ikke er administrator på den riktige avtalen.
Be om tillatelser i VLSC
Sjekk at du har rettigheter til å administrere avtalen. Gå til Administrasjon->Mine tillatelser og se om avtalen som lisensene er bestilt på dukker opp i listen her. Du finner avtalenummeret på kvitteringen som du har fått av din distributør.
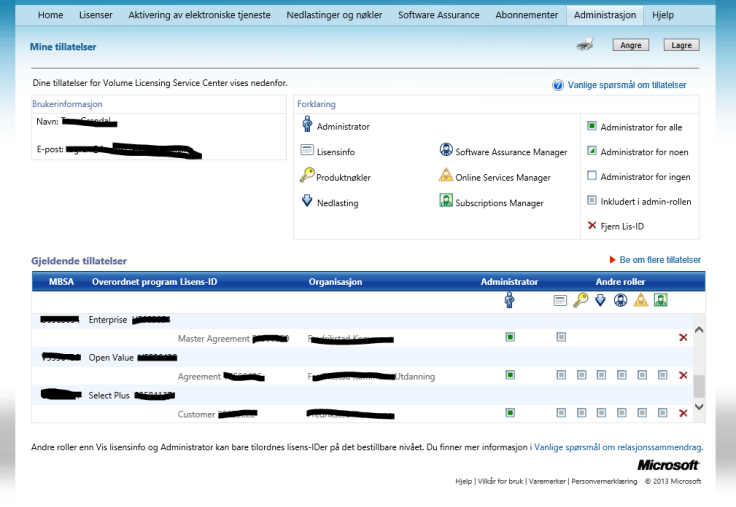
Dersom du ikke ser avtalen her så må du be om tilgang. Trykk da på Administrasjon->Be om tillatelser. Velg lisensprogrammet som det er bestilt på (står på kvitteringen) og skriv in lisensnummeret. Husk nå å hak deg av som Administrator så får du tilgang til alle de andre funksjonene også.
For å bli godkjent så må nå den riktige admistratoren logge inn med sin Microsoft konto og godkjenne deg. Hvis du ikke vet hvem dette er så spør du din distributør om hvem som er Online Contact and Notices.
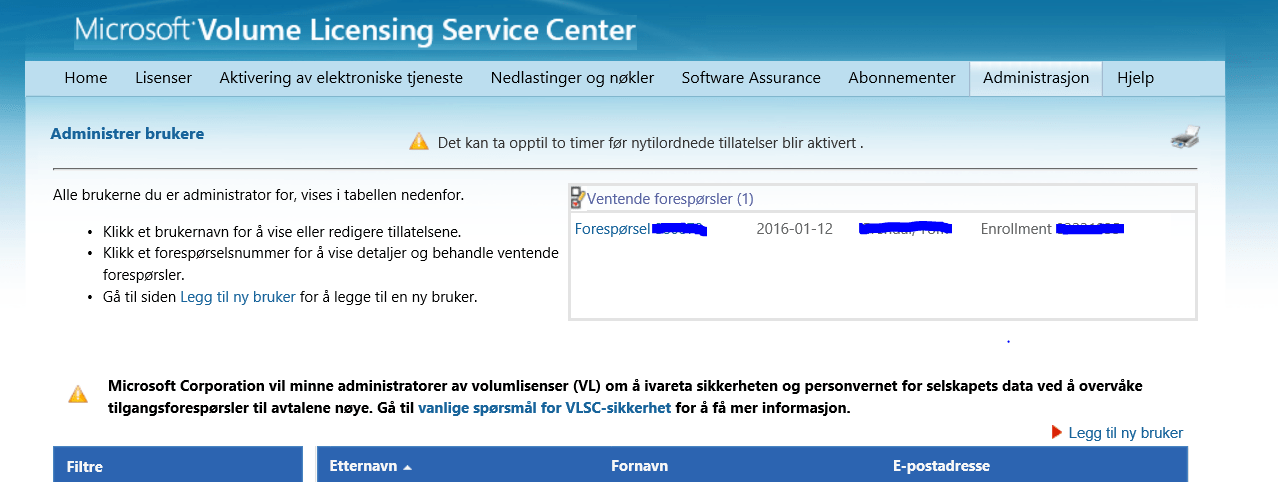
Denne personen må så gå til Administrasjon->Administrere Brukere
Når dette er gjort så venter du 2 timer og prøver igjen å logge deg på med din egen konto for å håndtere aktiveringen av de elektroniske tjenestene.
Nyttig? Vis det til flere!






















You must be logged in to post a comment.